In today’s digital landscape, data is the lifeblood of businesses and individuals alike. From personal information to financial records, the sheer volume and sensitivity of data being collected and stored makes it a prime target for cyberattacks. Protecting this data is no longer a matter of good practice; it’s a critical imperative for maintaining trust, complying with regulations, and ensuring business continuity. Effective data security strategies are no longer optional; they are fundamental to survival in the 21st century. This article will explore key strategies and best practices for bolstering your organization’s data security posture.

The Growing Threat Landscape

The rise of sophisticated cyber threats has dramatically increased the urgency of data security initiatives. Ransomware attacks, phishing scams, data breaches, and insider threats are all prevalent and increasingly costly. Statistics consistently demonstrate a significant rise in these incidents, highlighting the need for proactive and layered defenses. Data security isn’t just about preventing breaches; it’s about minimizing the impact when they do occur. Organizations that fail to adequately protect their data face significant financial losses, reputational damage, and legal repercussions. Furthermore, increasing regulatory scrutiny, such as GDPR and CCPA, adds another layer of complexity and necessitates robust compliance measures. Understanding the evolving threat landscape and adapting security measures accordingly is paramount.
Implementing Strong Access Controls
One of the most fundamental aspects of data security is establishing and enforcing robust access controls. This involves carefully defining who has access to what data and ensuring that access is granted only to those who need it. Implementing the principle of least privilege – granting users only the minimum level of access required to perform their job duties – significantly reduces the potential damage from compromised credentials or insider threats. Multi-factor authentication (MFA) should be mandatory for all users accessing sensitive data, adding an extra layer of verification beyond just a password. Regularly reviewing and updating access permissions is crucial to maintain effectiveness. Consider utilizing role-based access control (RBAC) to simplify management and ensure consistent application of security policies. Poorly configured access controls are a common entry point for attackers.

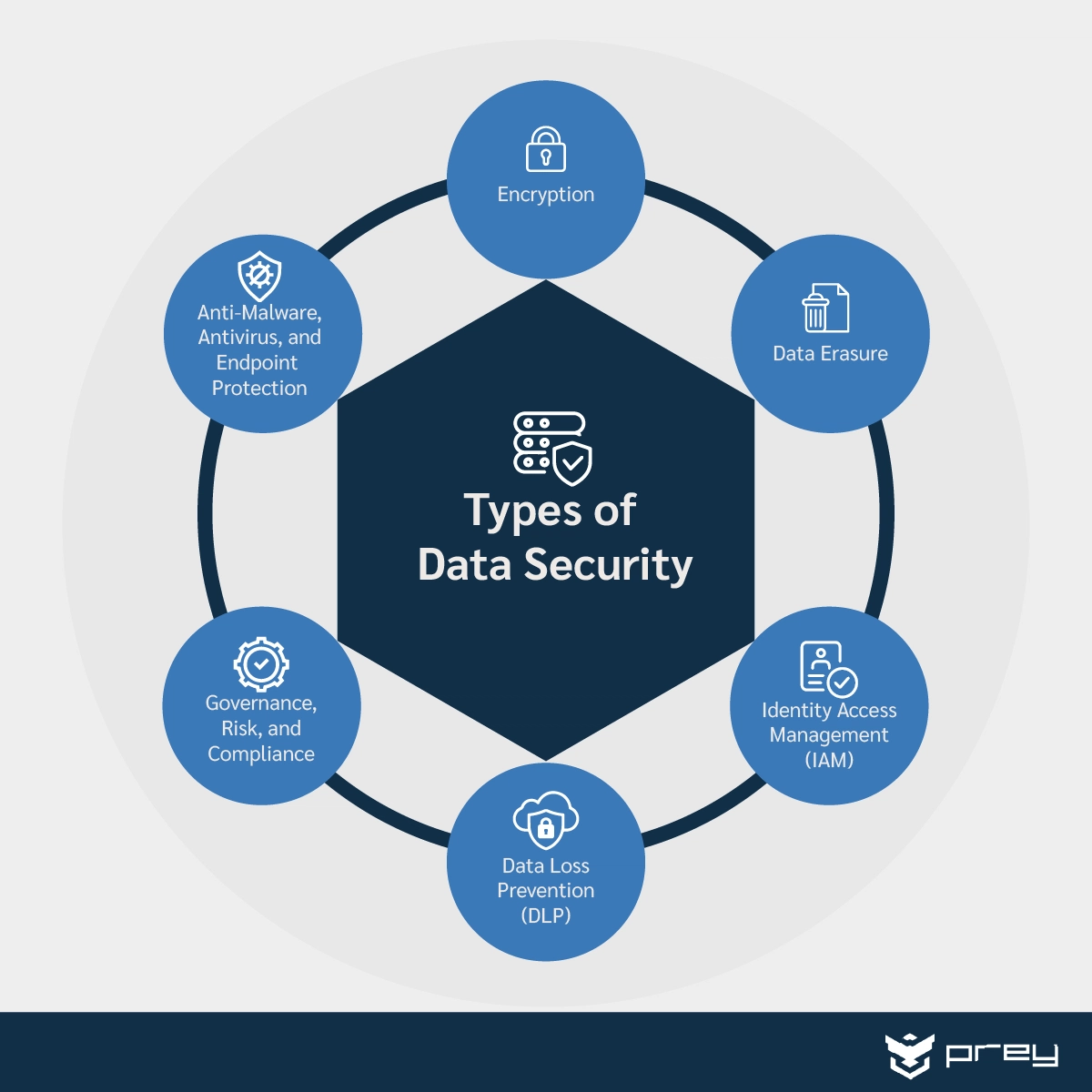
Data Encryption – Protecting the Data at Rest and in Transit
Data encryption is a cornerstone of data security. Encrypting data both at rest (when stored on devices and servers) and in transit (when being transmitted over networks) renders it unreadable to unauthorized individuals, even if they manage to intercept it. Using strong encryption algorithms and managing encryption keys securely are essential. Consider using full-disk encryption for laptops and mobile devices, and encrypt sensitive files and databases. Proper key management is critical; lost or compromised keys render encryption ineffective. Furthermore, utilizing TLS/SSL for all web traffic and VPNs for remote access adds a crucial layer of protection. Regularly auditing encryption configurations is vital to identify vulnerabilities and ensure compliance.

Employee Training and Awareness – The Human Element
Human error is often the weakest link in a data security chain. Data security strategies are only as effective as the people who implement them. Comprehensive employee training programs are essential to educate users about phishing scams, social engineering tactics, and safe data handling practices. Regular phishing simulations can help employees identify and avoid these attacks. Promoting a culture of security awareness, where employees are encouraged to report suspicious activity, is equally important. Simultaneously, providing clear and concise policies regarding data handling, password management, and acceptable use of company resources can significantly reduce risk. Training should be ongoing and tailored to specific roles and responsibilities.

Network Security – Segmentation and Firewalls
Network security is a critical component of data protection. Segmenting your network into different zones – for example, separating sensitive data from less critical systems – limits the potential impact of a breach. Firewalls act as a barrier between your network and the outside world, blocking unauthorized access and inspecting network traffic. Regularly updating firewall rules and monitoring network activity for suspicious patterns is crucial. Implementing intrusion detection and prevention systems (IDS/IPS) can help identify and block malicious traffic before it reaches your systems. Consider using Virtual Private Networks (VPNs) to secure remote access to the network. Properly configuring network access controls and utilizing network segmentation are key to minimizing the attack surface.

Data Loss Prevention (DLP) – Monitoring and Preventing Data Exfiltration
Data Loss Prevention (DLP) tools help organizations monitor and prevent sensitive data from leaving their control. DLP solutions can analyze data in motion and at rest, identifying and blocking unauthorized transfers. These tools often integrate with email, cloud storage, and other data sources. Implementing DLP policies that define acceptable data handling practices and monitor for data exfiltration attempts is essential. Regularly reviewing DLP policies and adjusting them based on evolving threats is crucial. Understanding the different types of data that are most vulnerable to loss and implementing appropriate safeguards is a key aspect of DLP implementation.

Regular Backups and Disaster Recovery – Ensuring Business Continuity
Data loss can be devastating, and having a robust backup and disaster recovery plan is essential for minimizing the impact. Regularly backing up data to offsite locations ensures that you can recover from a ransomware attack, hardware failure, or other disaster. The backup process should be tested regularly to ensure its effectiveness. A comprehensive disaster recovery plan should outline the steps required to restore critical systems and data within a defined timeframe. Consider using cloud-based backup solutions for increased scalability and resilience. Having a well-defined recovery plan is not just about recovering data; it’s about restoring business operations.

Compliance and Regulatory Considerations
Many industries are subject to strict data security regulations. Compliance with regulations like GDPR, HIPAA, and CCPA requires organizations to implement specific security measures. Data security strategies must be aligned with these regulations. Conducting regular audits and assessments to ensure compliance is crucial. Maintaining detailed records of security controls and data processing activities is also essential. Staying informed about changes in regulations and adapting security measures accordingly is a continuous process. Failure to comply can result in significant fines and legal penalties.

The Importance of Security Awareness Training – A Continuous Effort
Security awareness training is not a one-time event; it’s an ongoing effort. Employees need to be continuously educated about emerging threats and best practices. Regular phishing simulations, security awareness newsletters, and interactive training sessions can help reinforce security knowledge. Encouraging employees to report suspicious activity and fostering a culture of security responsibility are equally important. A proactive approach to security awareness is far more effective than reactive measures.
Conclusion
Data security is a dynamic and evolving challenge. Data security strategies must be continuously reviewed and adapted to address emerging threats and changing regulations. A layered approach, combining technical controls, employee training, and robust policies, is essential for protecting valuable data assets. Investing in a comprehensive data security program is not just a cost; it’s an investment in the long-term success and resilience of your organization. By prioritizing data security, businesses can mitigate risks, maintain trust, and ensure a competitive advantage in today’s digital world. Ultimately, a proactive and informed approach to data security is the key to navigating the complexities of the modern threat landscape.